Attribute & Role Mapping
It is the on-the-fly assignment of specific attributes/roles to your users as they are present in your IDP. When the user performs the SSO, the IDP sends over some attributes like NameID, Email, etc. which are then used to assign the users with specific functionalities like access or restrict the resources. The Attribute/Role Mapping section allows you to enable these certain property-specific functionalities for your users during SSO.
This section contains the following 3 sections:
1. Attribute Mapping
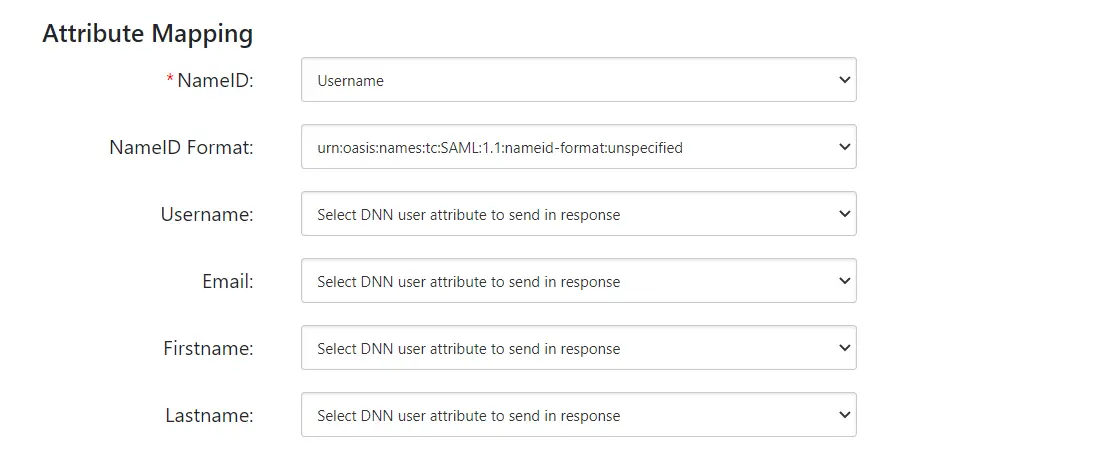
Attributes are the user details that are stored in your identity provider. These attributes include Username, Email, First Name, Last Name, Group/Role, Display Name, etc. The Attribute Mapping feature helps you to map these DNN user attributes sent by the IDP to the user attributes on SP.
-
Every time a user SSO into your application, these DNN user attributes will be automatically mapped to your application’s user profile.
-
If any existing user performs the SSO, then their application account will be fetched and their profile will be updated based on attributes received from the IDP.
-
By default, the Username and Email are the two basic attributes that are used for attribute mapping. Generally, the NameID value is what’s used for this purpose.
-
You can choose and set attributes sent by the IDP to be mapped with attributes like FirstName and LastName.
-
The Group/Role field can be used as a group transformation attribute. You can map the Group/Role field to the attribute name in which IDP is sending the DNN user’s Information.
-
Depending on the value of the Group attribute, you can assign single or multiple roles to the users. Custom roles are also supported for the mapping. Please refer to the role mapping section for more information.
Map Custom Attributes
-
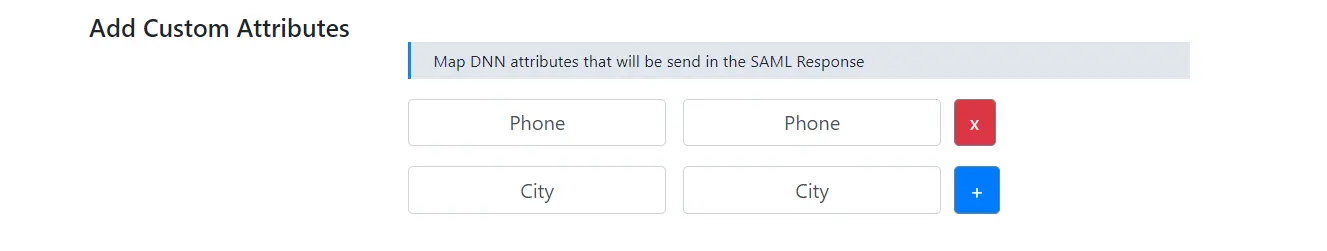
It provides an additional feature to Map Custom Attributes to the DNN users. Using this feature you can map and access additional attributes received from the IDP in your application.
-
Suppose, you want to map attributes like Phone no., City, State, or Department, etc., you will simply have to add these attributes in your IDP and set them up into your Custom attribute mapping to map with their equivalent attributes.
-
For example, the image below shows the above attributes which are sent from the identity provider appropriately added and mapped to their equivalent attributes name.
2. Role Mapping
-
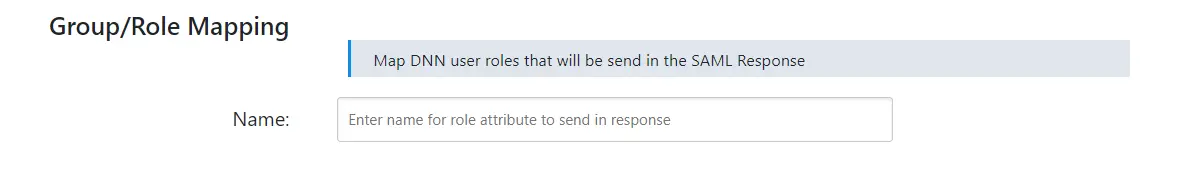
This feature can be used to assign different roles to the users based on their SAML attributes. The DNN user roles will be applied to your users once they meet the specified conditions while logging into your service provider application via Single Sign-On.
-
This feature allows you to provide user capabilities based on their IDP attribute Group values.
-
Before enabling this setting, please make sure you’ve configured the attribute name in the Group/Role field of the Attribute Mapping section.
-
If the admin wants users of a particular IDP group(s) to be restricted from logging in to the site, this feature can be enabled by providing the group value(s).
-
This feature can be used where we have a group of students with Off-Campus Registration. They have been assigned an IDP group Outside Users and the admin does not want those users to access the site.