OAuth Tokens
Authorization Grant
Implementing third-party access tokens for authenticating REST APIs is a robust and secure approach that mitigates the risk of exposing user credentials. This method not only enhances security but also facilitates access revocation, offering a flexible solution for scenarios involving the integration of third-party applications. By utilizing third-party access tokens, you establish a more streamlined and scalable authentication process. This not only improves the overall security posture of your REST APIs but also ensures a level of flexibility that is essential when dealing with diverse and dynamic third-party integrations. Overall, adopting this method contributes to a more resilient and secure ecosystem for your API interactions.
You can effortlessly configure popular third-party providers or use the custom provider option if you have your provider.

Sample Request
Request: GET /rest/api/2/myself
Header: Authorization : Bearer <token>
Success Response
- Table for success response
| Code | Error | Description |
|---|---|---|
| 200 | Ok | { "self": "http://localhost:8080/rest/api/2/user?username=admin", "key": "JIRAUSER10000", "name": "admin", "emailAddress": "admin@gmail.com", "displayName": "admin", "active": true, "deleted": false, "timeZone": "Asia/Calcutta", …………} |
Error Response
- Table for error responses
| Code | Error | Description |
|---|---|---|
| 400 | BAD REQUEST | You will get this error when the user with username returned from the provider is not present in the user directory { "error": { "status": "ERROR", "message": "No user found with this username/email address" } } |
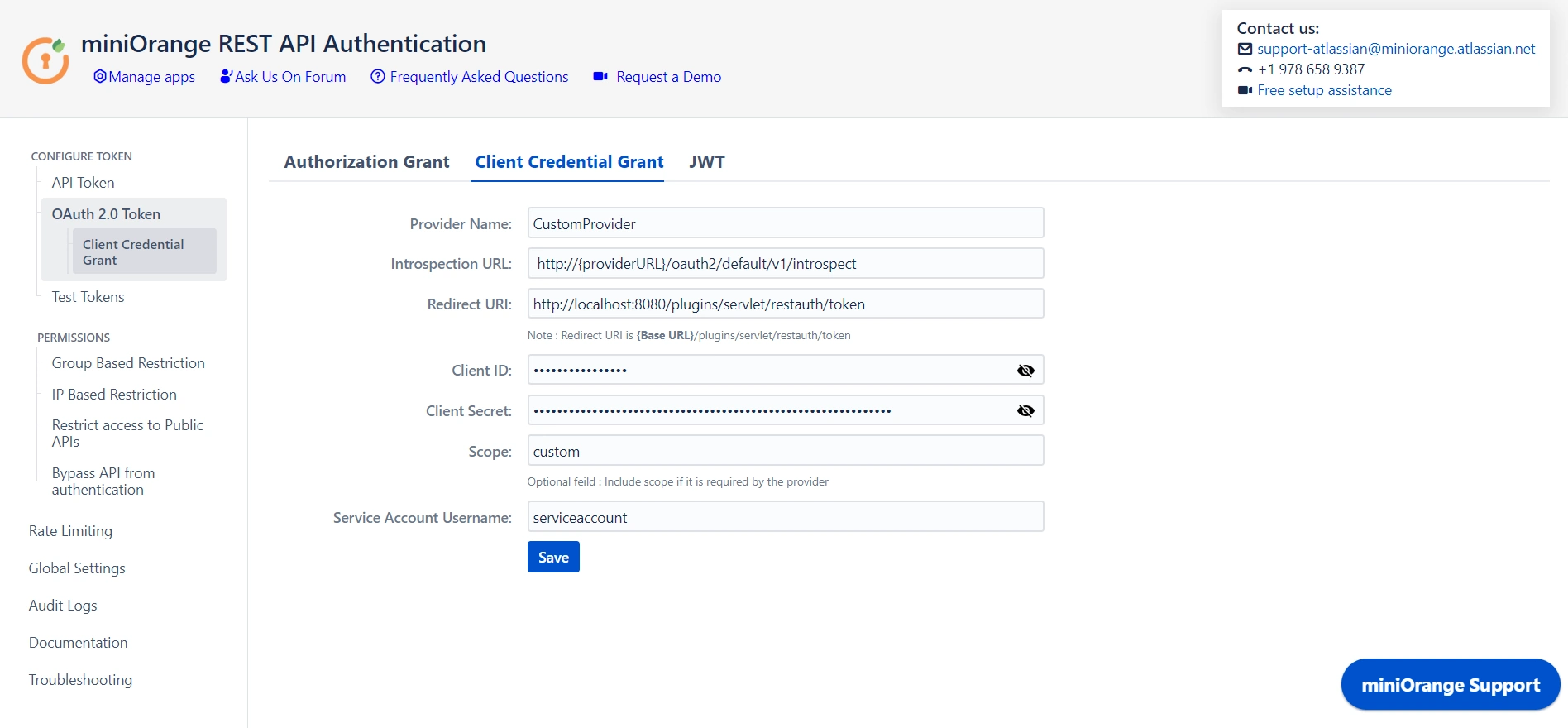
Client Credentials Grant
The Client Credentials Grant is a valuable authorization mechanism designed for scenarios where APIs are accessed by trusted clients without the need for user involvement. This grant type is particularly suitable for server-to-server communication or machine-to-machine interactions, offering a streamlined and secure approach to authentication. Since this grant type operates without direct user interaction, it is well-suited for backend processes and services that require secure and seamless access to API resources. The Client Credentials Grant enhances the efficiency of server-to-server communication, providing a robust foundation for authenticating trusted clients within the API ecosystem.
You can configure the token provider and set up a service account to use the client credential grant.
Sample Request
Request: GET /rest/api/2/myself
Header: Authorization : Bearer <token>
Success Response
- Table for success response
| Code | Error | Description |
|---|---|---|
| 200 | OK | { "self": "http://localhost:8080/rest/api/2/user?username=admin", "key": "JIRAUSER10000", "name": "admin", "emailAddress": "admin@gmail.com", "displayName": "admin", "active": true, "deleted": false, "timeZone": "Asia/Calcutta", .............. } |
Error Response
| Code | Error | Description |
|---|---|---|
| 401 | UNAUTHORIZED | You will get this error when configured client ID/client secret is wrong or you are accessing API using an expired token { "error": { "status": "ERROR", "message": "Expired Token / invalid_client_ID" } |
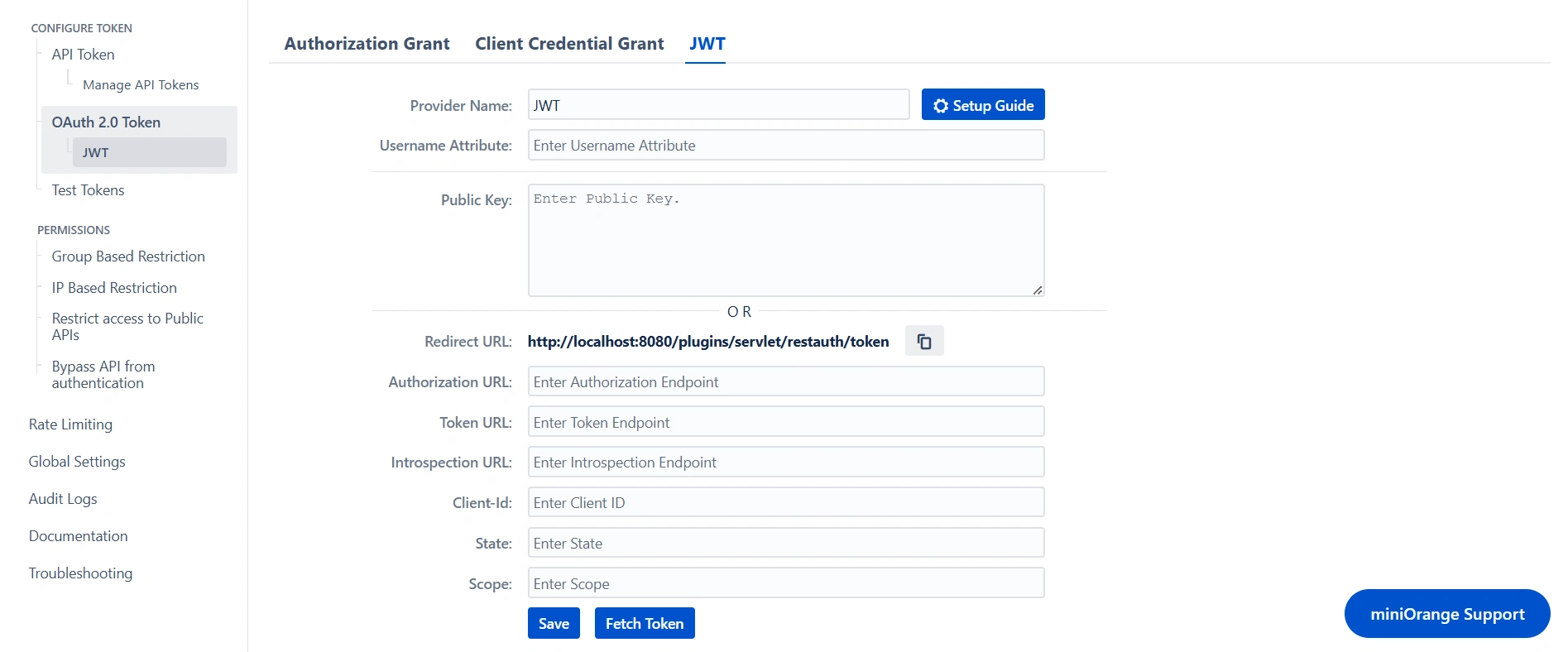
JWT
JSON Web Tokens (JWTs) are widely used for representing claims and securely transmitting information related to the client or user's identity. When securing REST API, using JWT is a reliable option. This method allows for the generation of JWTs using private keys or obtaining them from a trusted third-party provider and then using them to access REST APIs. By incorporating JWTs into the authentication process, you enhance the integrity of your REST API, as they serve as a secure and efficient means of conveying identity-related data.
To authenticate REST APIs using JWTs, you need to configure either the public key for decoding the token or set up a third-party provider that will provide the tokens and validate them using the introspection endpoint.
Sample Request
Request: GET /rest/api/2/myself
Header: Authorization : Bearer <token>Success Response
- Table for success response
| Code | Error | Description |
|---|---|---|
| 200 | OK | { { "self": "http://localhost:8080/rest/api/2/user?username=admin", "key": "JIRAUSER10000", "name": "admin", "emailAddress": "admin@gmail.com", "displayName": "admin", "active": true, "deleted": false, "timeZone": "Asia/Calcutta", …………} |
Error Response
- Table for error responses
| Code | Error | Description |
|---|---|---|
| 400 | BAD REQUEST | You will get this error if you have entered an invalid token, there is an error while parsing the JWT. { "error": { "status": "ERROR", "message": "Token Invalid: Error while validating the token." } } |
| 400 | BAD REQUEST | You will get this error if a user with the username fetched from JWT does not exist. { "error": { "status": "ERROR", "message": "No user found with this username/email address" } } |
| 401 | UNAUTHORIZED | You will get this error if you are accessing API using an expired token<br>{ "error": { "status": "ERROR", "message": "Token Expired: The token provided is expired." } } |