Sign In Setting
Enable SSO
Enabling this option will allow all your Jira software users to perform SSO. If this option is disabled, then the SSO for all the users is disabled. You can use this feature to test SSO on your environment without affecting the end users by disabling the SSO for all. Enabling/disabling this feature will override your IdP specific Enable SSO for Jira Software settings you have configured in the IdP menu.
Enable Header Based Authentication
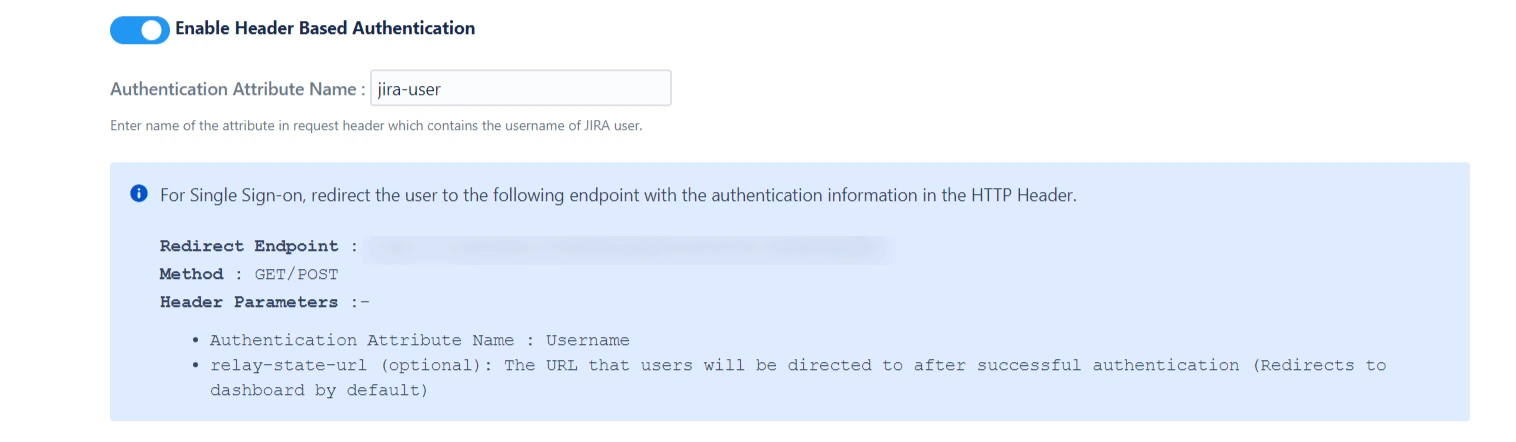
Authenticate users based on the user’s information (username) received in the HTTP headers.This feature is commonly used in settings where a reverse proxy/vpn is used and it requires user authentication.
Enabling header based authentication allows users to log in automatically based on the request header. If you or your company uses a reverse proxy or VPN, but you still require user authentication, then this setting should be enables.
When header authentication is enabled, the plugin will authenticate the user into the application without prompting for the credentials again.
Login Button Text
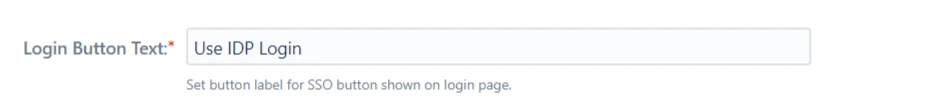
Customize SSO button text as per requirement using this option ( This text is visible only in case of Single IdP.)
Relay State URL
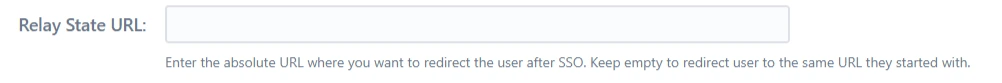
Enter the absolute URL where you want to redirect the user after SSO. Keep empty to redirect user to the same URL they started with.
Auto Redirect to IdP
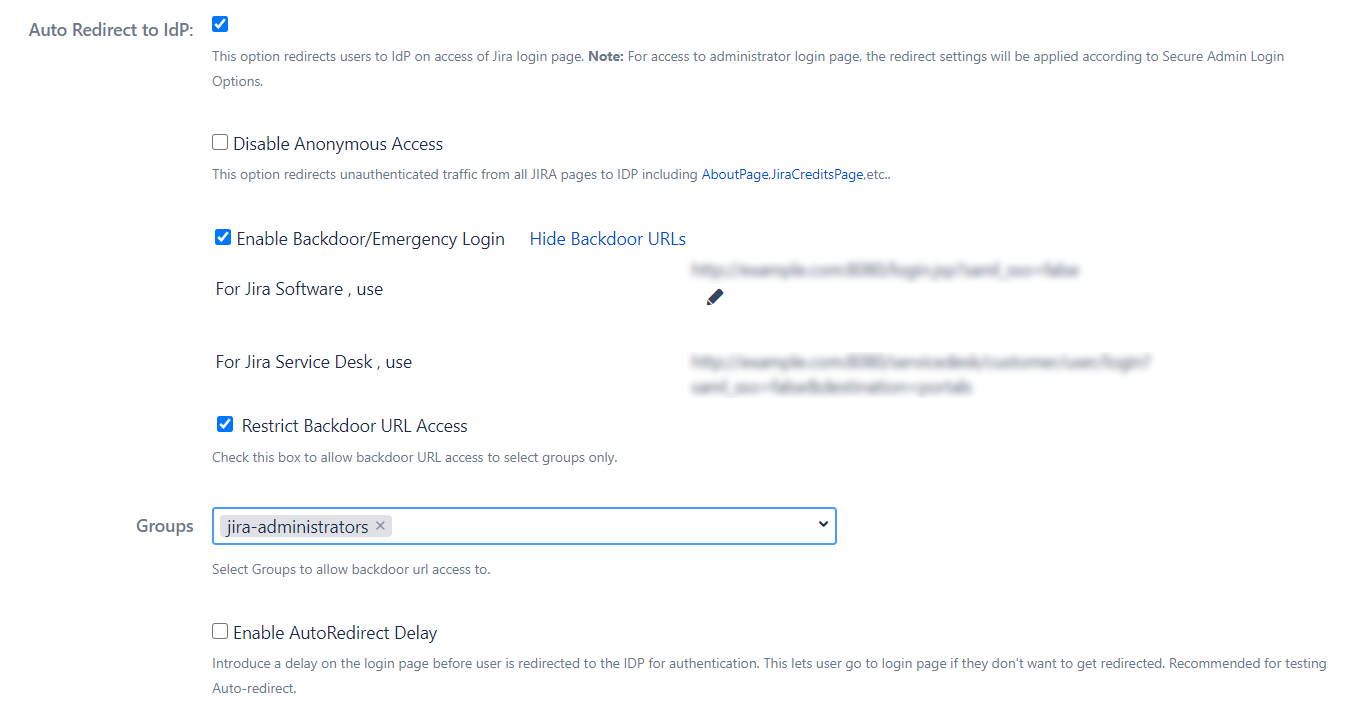
On enabling this option, all unauthenticated users are automatically redirected to the SSO login page. Enable this option if you want to force the authentication of all the users to be done through SSO and not allow the users to use the login functionality provided by the application.
Let us consider Okta as IdP, when the user triers to access the login page of the application he will be redirected to the Okta login page, and after successful login he will be redirected to the page he started of.
Disable Anonymous Access
Some pages in the Atlassian applications can be accessed by unauthenticated traffic like public filters, public spaces, About pages, etc. Also, there are some pages that are not available to unauthenticated users but don’t prompt login and just show an error message.
Disabling Allow Access to Anonymous Pages without SSO switch makes sure that all unauthenticated traffic on your application is prompted for login before being able to view such pages.
Restrict Backdoor URL Access
You can Restrict the Backdoor URL to certain groups in the application. When you enable this option, you’ll be asked to enter the groups to whom backdoor access should be provided. Now, when a user tries to access the backdoor URL, he’ll be asked for his username first and if that username belongs to the configured group, only then will he be able to use the login page.
Enable Backdoor/Emergency Login
Backdoor/Emergency URL can be used by local administrators to access the login page when SSO is enabled. This is useful when you’ve Redirection Rules set or when the Default Rule doesn’t have the login page selected.
You can customize the Backdoor URL by clicking on the edit button beside it and entering new parameter values.
Enable backdoor using REST API
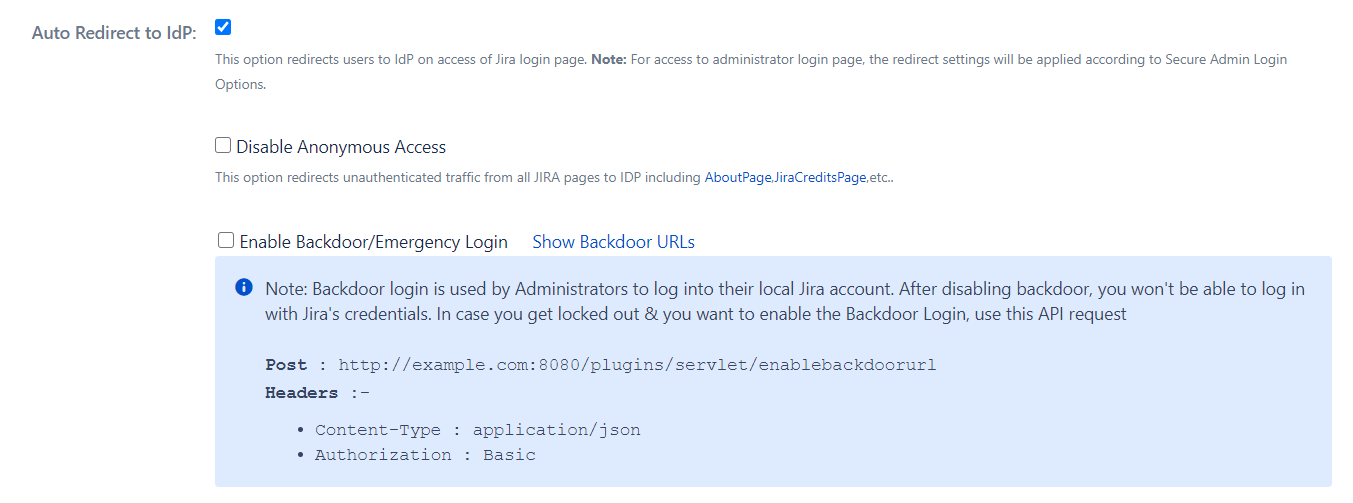
Backdoor login is used by Administrators to log into their local Jira account. After disabling backdoor, you won't be able to log in with Jira's credentials. In case you get locked out & you want to enable the Backdoor Login, use this API request.
Enable AutoRedirect Delay
If you have just one IdP set as default IdP in the Redirection Rules, the user is redirected for SSO as soon as he accesses the application. To add a delay here, you can enable this option. In this case, a progress bar will be shown on the login page which will allow users to cancel redirection and use application credentials to log in.
Secure Admin Login Options
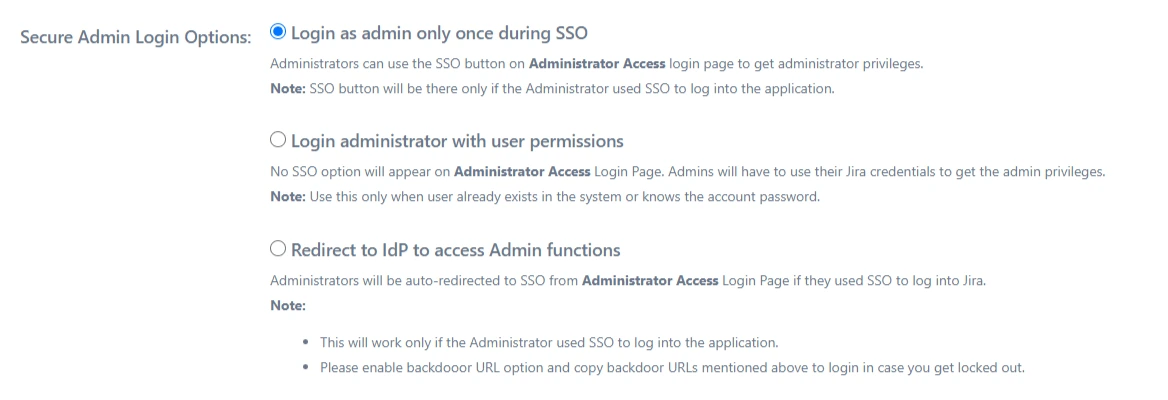
Login as admin only once during SSO
User’s admin session will be created on the first login. When the admin session expires, the administrator won’t be redirected to IdP. Instead, the admin login page will be shown.
Login administrator with user permissions
User’s admin session will not be created on the first login. Additionally, the administrator will not be redirected to IdP on access to the administration console.
Note: Use this only when the user already exists in the system or knows their account’s password.
Redirect to IdP to access Admin functions
User’s admin session will be created on the first login. Also, the user will always be redirected to provider on the access of the admin console.
Note: Please enable backdoor URL option and copy backdoor URLs mentioned above to login just in case a lock out situation occurs.