Advanced Options
User Flow Configurations
As you fine-tune your 2FA setup, it's essential to consider how users interact with these configurations to ensure both security and usability. The following user flow configurations allow administrators to manage and optimize how users engage with their 2FA settings, providing a balance between security enforcement and user flexibility.
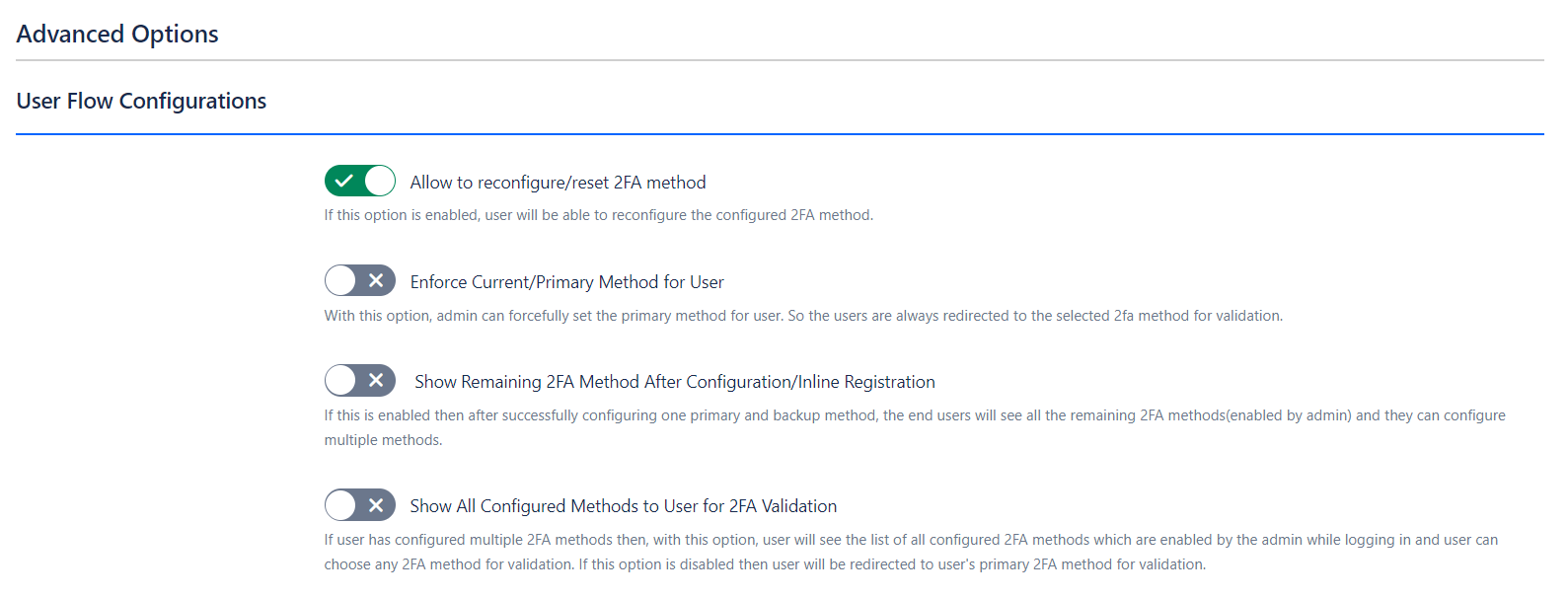
-
Allow Reconfigure/Reset 2FA:
-
Functionality: Enabling this option allows users to reset and reconfigure their 2FA settings through the Two Factor Configurations page in their user profile. Users can manage all available 2FA methods and update their settings, including backup codes.
-
Benefit: Offers users flexibility to update their 2FA settings as needed, maintaining effective account security.
-
-
Enforce Primary Method for Users:
-
Functionality: This setting is crucial when the admin needs to enforce a specific primary authentication method for users.
For example, Suppose the admin has enabled both the Mobile Authenticator and Yubikey Hardware Token methods. Users will configure both methods and, typically, choose one for primary authentication. With this feature enabled, the admin can mandate which 2FA method users must use for verification.
-
Benefit: Ensures a standardized and secure authentication experience, with backup options available if the primary method is not viable.
-
-
Show Remaining 2FA Methods After Configuration:
-
Functionality: When multiple methods are allowed by the admin and this option is enabled, users will be able to configure additional authentication methods after setting up their primary and backup methods.
-
Benefit: Encourages users to set up multiple authentication methods, enhancing security with additional layers of protection.
-
-
Show All Configured Methods to Users for Validation:
-
Functionality: This option displays all configured authentication methods to users during login, allowing them to select their preferred method for validation.
-
Benefit: Provides flexibility for users to authenticate using any configured method, ensuring access even if one method is unavailable.
-
Brute Force Protection
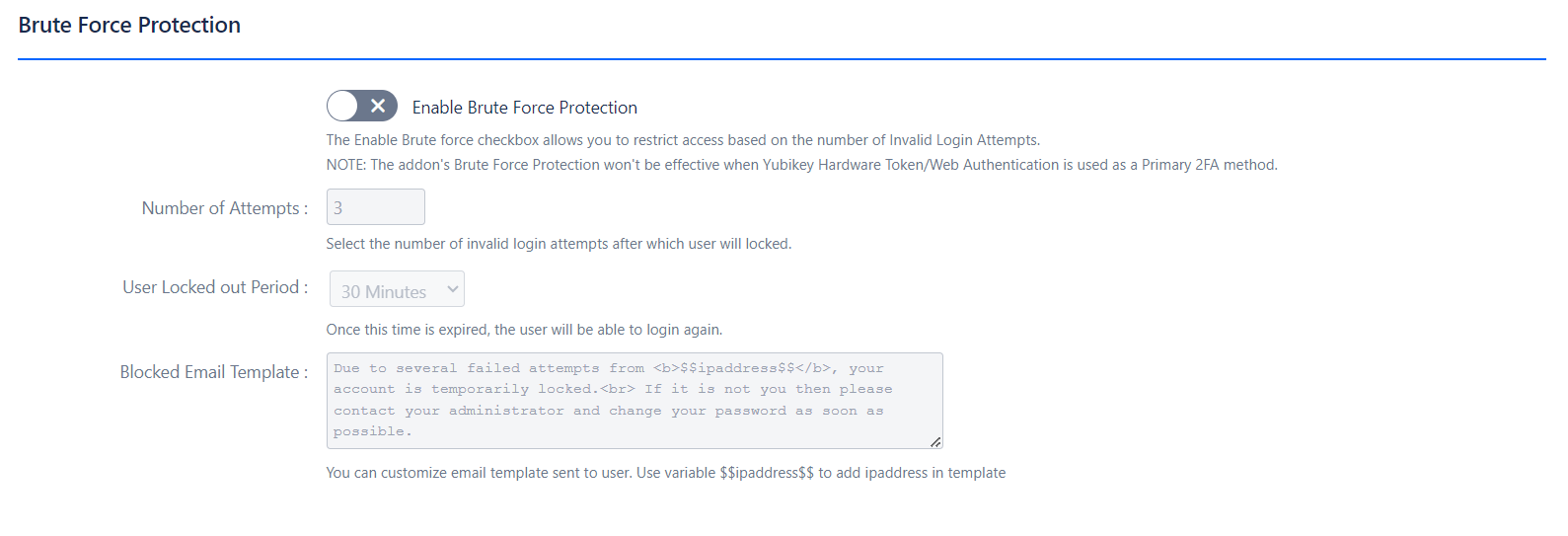
-
Functionality: Brute Force Protection restricts access to Confluence after a specified number of invalid login attempts, enhancing security by locking out users who fail to authenticate repeatedly.
-
Benefits:
-
Prevents Unauthorized Access: Helps protect against brute force attacks by limiting login attempts.
-
Customizable Lockout Period: Allows setting a lockout period to control how long a user is prevented from logging in.
-
Note: This feature is not effective when Yubikey Hardware Token/Web Authentication is used as the primary 2FA method.
Multilingual Support
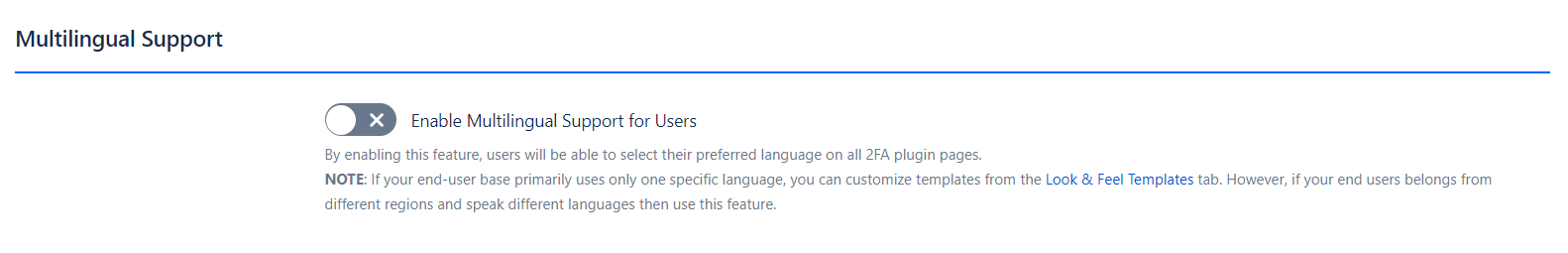
-
Functionality: Enables users to select their preferred language on all 2FA plugin pages, accommodating diverse user bases with different language preferences.
-
Benefits: Enhanced User Experience: Provides a personalized experience for users from various linguistic backgrounds.
Note: For organizations with a predominantly single-language user base, you can customize templates in the Look & Feel Templates tab. For a multilingual user base, enabling this feature is recommended.
Remember My Device
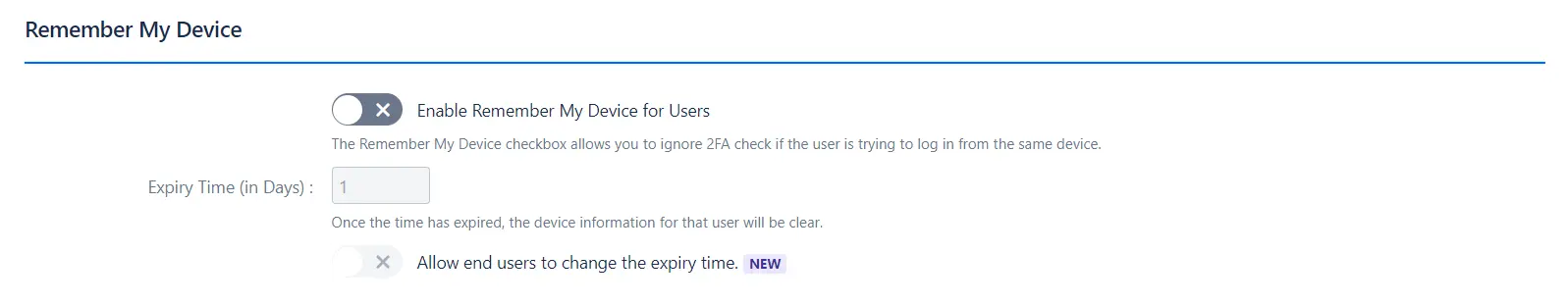
-
Functionality: Allows users to bypass the 2FA check when logging in from the same device, improving user convenience and reducing the frequency of 2FA prompts.
-
Benefits:
-
Convenience: Users can avoid repetitive 2FA requests when using the same device.
-
Customizable Expiry: Set the duration for which the device will be remembered, or allow users to adjust this setting.
-
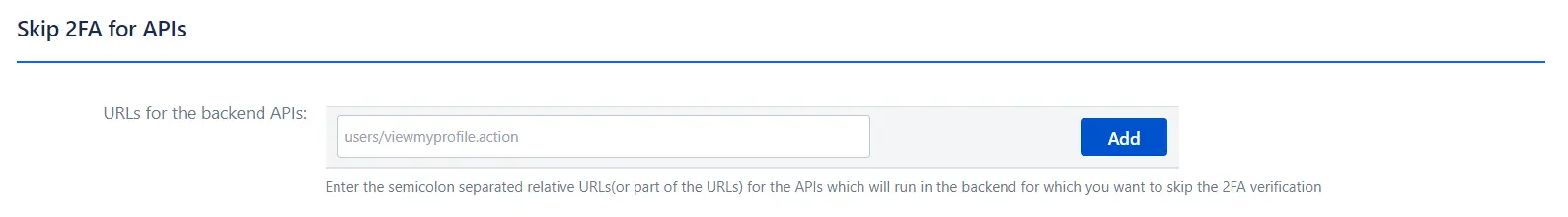
Skip 2FA for APIs
-
Functionality: Enables skipping 2FA for specific backend APIs, streamlining interactions for internal systems.
-
Benefits:
- Operational Efficiency: Facilitates smoother internal processes by excluding certain API calls from 2FA requirements.
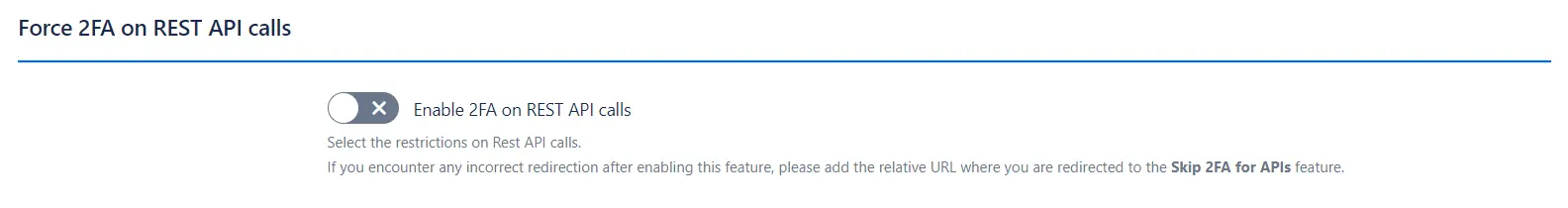
Force 2FA on REST API Calls
-
Functionality: Enforces 2FA on REST API calls to ensure additional security for API interactions.
-
Benefits:
- Increased Security: Adds an extra layer of protection for REST API interactions, reducing the risk of unauthorized access.
Note: If redirection issues arise after enabling this feature, add the redirected URL to the Skip 2FA for APIs feature.
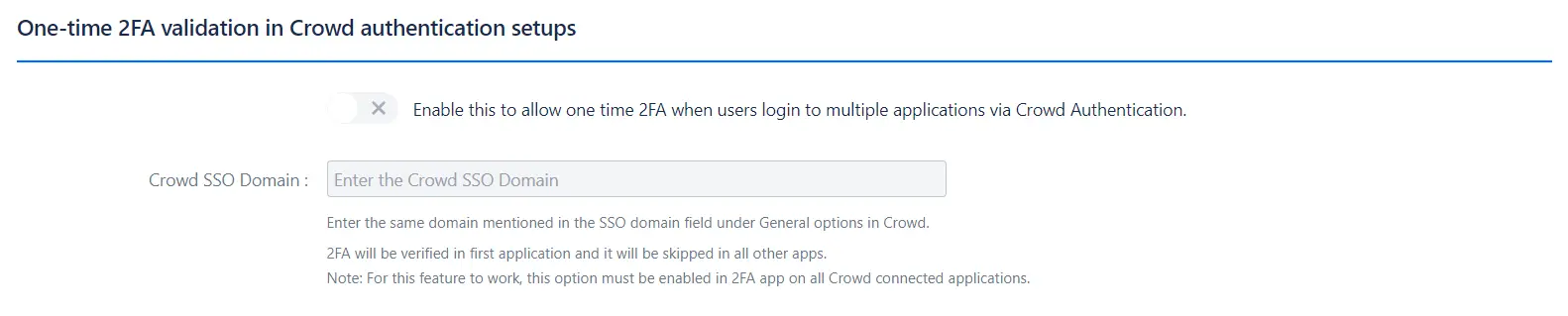
One-Time 2FA Validation in Crowd Authentication Setups:
-
Functionality: Allows one-time 2FA validation when users log into multiple applications via Crowd Authentication, simplifying the login process across applications.
-
Benefits:
- Streamlined Authentication: Reduces the need for repeated 2FA prompts across multiple applications.
Note: This feature must be enabled in the 2FA app for all Crowd-connected applications.
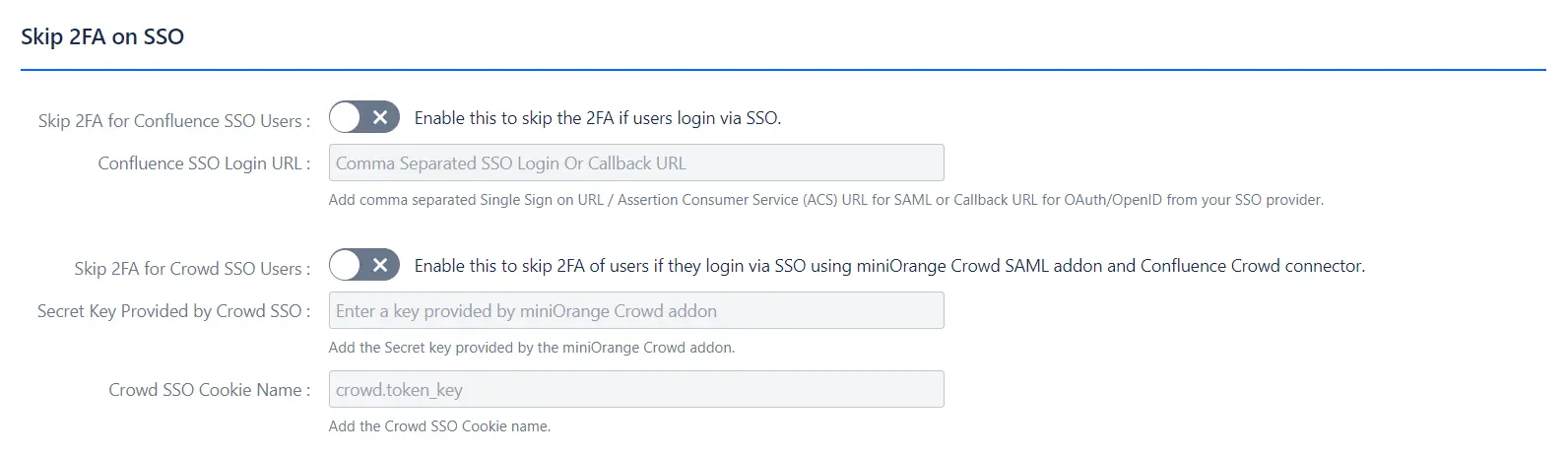
Skip 2FA on SSO
-
Functionality: Allows skipping 2FA for users logging in via Single Sign-On (SSO), enhancing convenience while using SSO.
-
Benefits:
- User Convenience: Reduces the frequency of 2FA prompts for users authenticated through SSO.
Note: For Crowd SSO, additional configuration such as entering the secret key and cookie name is required.
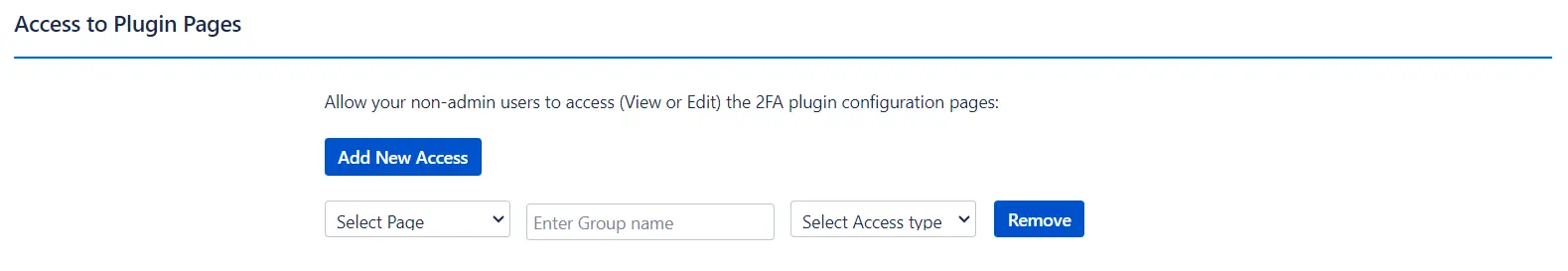
Access to Plugin Pages
-
Functionality: Controls access to the 2FA plugin configuration pages for non-admin users, allowing selective access based on user groups.
-
Benefits:
- Controlled Access: Provides the ability to manage who can view or edit the 2FA plugin settings.
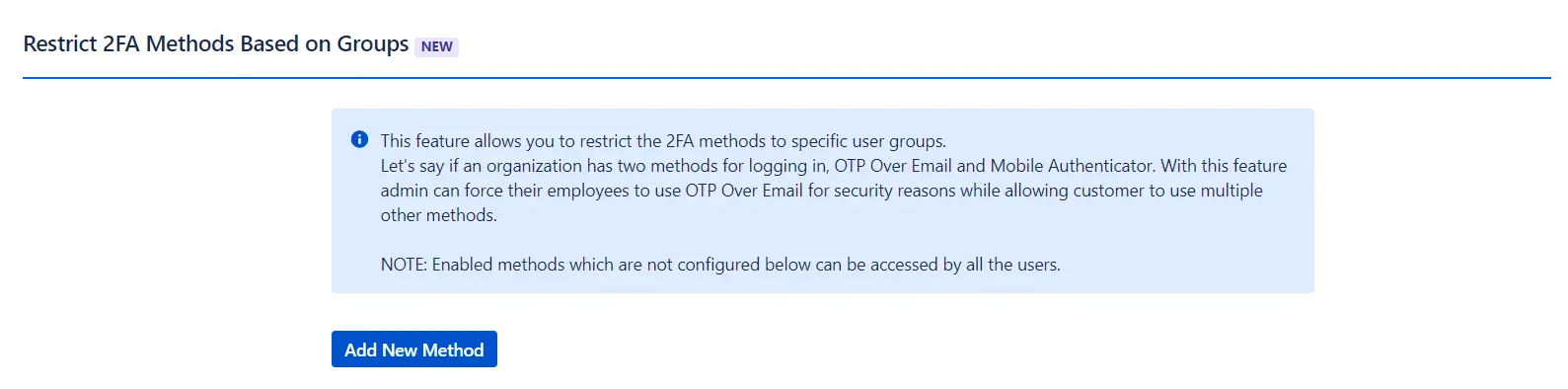
Restrict 2FA Methods Based on Groups
-
Functionality: Allows restriction of 2FA methods to specific user groups, ensuring that different groups use designated methods according to security policies.
-
Benefits:
- Policy Enforcement: Ensures compliance with organizational security policies by mandating specific 2FA methods for different user groups.
Note: Enabled methods that are not configured for specific groups will be accessible to all users.