Yubikey Hardware Token(U2F/WebAuthn)
Universal Second Factor (U2F) is a highly secure 2FA method recognized by cybersecurity experts as one of the most effective mechanisms for protecting accounts. It relies on public-key cryptography and offers robust resistance against phishing attacks. This method is also user-friendly, making it a popular choice for enhancing security.
1. How U2F Works
-
Public-Key Cryptography: U2F uses a pair of cryptographic keys—a private key stored securely on the hardware token and a public key registered with the server. During authentication, the hardware token uses the private key to sign a challenge from the server, proving the user’s identity.
-
Hardware Token Use: To authenticate, users simply insert the U2F key into a USB port and press a button on the token. This action generates a cryptographic response that the server verifies against the registered public key.
2. Configuration Process
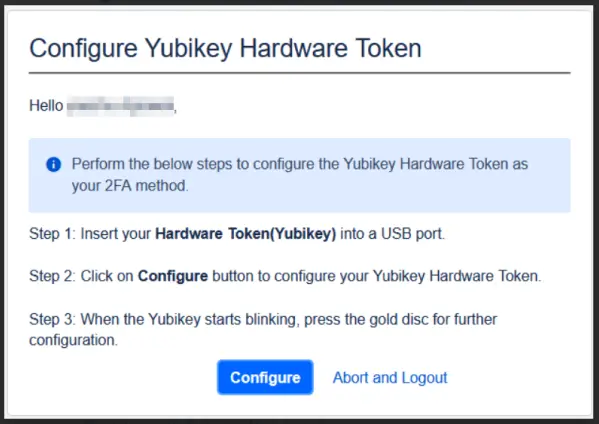
-
Registration:
-
Private Key Generation: When a user registers their U2F hardware token, a private key is generated for encryption.
-
Token Confirmation: During the registration process, users confirm the request by pressing a button on the hardware token. This step binds the hardware token to the user’s account by associating the generated private key with their account.
-
-
Authentication:
-
Token Insertion and Verification: To log in, users insert the hardware token into the USB port. The token then generates a response using the stored private key.
-
Button Press: Users must press the button on the token to complete the authentication process. This action provides the server with a cryptographic proof of the user’s identity.
-
3. Security Benefits
-
Phishing Resistance: Unlike software-based 2FA methods, U2F hardware tokens are highly resistant to phishing attacks because the token itself must be physically present to authenticate. An attacker cannot access the account without the actual hardware token.
-
Hardware Token Security: U2F relies on physical security keys, which are less susceptible to hacking attempts compared to software-based solutions. These keys generate a unique pair of keys for each service, enhancing the security posture by preventing the sharing of secrets among service providers.
Note: This 2FA method requires SSL to be set up on your Atlassian instance for secure communication.
For detailed instructions on configuring a Yubikey hardware token, please refer to our 2FA setup guide.