Security Questions(KBA)
The Security Questions (Knowledge-Based Authentication or KBA) method enhances security by requiring users to provide answers to personal questions that are known only to them. This authentication method adds a layer of protection by leveraging personal knowledge.
How Security Questions Work
-
Configuration
-
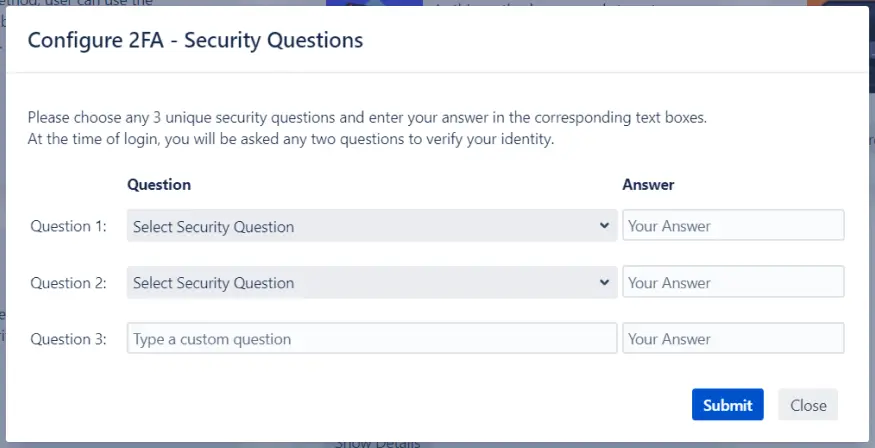
Set Up Questions: Users configure three unique security questions during registration. These questions should be personal and known only to the user.
-
Provide Answers: Users input answers to these questions, which are securely stored for later verification.
-
-
Authentication Process
-
Question Selection: Upon logging in, users are prompted to answer any two of the three security questions they previously configured.
-
Correct Answers Required: Users must answer the selected questions correctly to gain access. If the answers do not match the stored responses, access is denied.
-
Security Considerations
-
Question Selection: Choose questions that are difficult for others to guess but easy for you to remember. Avoid questions with answers that can be found through social media or public records.
-
Answer Security: Ensure that answers are not easily guessable or predictable. Consider using a combination of random characters or personal information that is not publicly available.
For detailed instructions on setting up and configuring Security Questions, please refer to the 2FA setup guide.