Custom Certificates
In SAML SSO, the Service Provider and the Identity Provider exchange data using SAML requests and responses. To secure these transactions you can sign your requests and enable encryption for responses received from the Identity Provider. A Keypair of the public and private X.509 certificate is used to sign SAML Single Sign-On/ Logout Request and to decrypt SAML Assertion/Response from the Identity Provider(IdP).
The public key provided in the add-on(SP) is used by the IdP to correctly identify the SP sending the request. The SP sends SAML requests by signing them. This makes sure that a third party system can’t forge the SAML request and makes it impossible to change data in the SAML request through attacks like the man in the middle attack.
The public key of SP is also used by the IdP to encrypt the assertion data which can be decrypted by the add-on only. This encryption ensures that no one else gets access to sensitive information about users sent in the SAML response.
We have pre-configured the public and private certificates for you to get started quickly, but you also can use your own custom certificates to increase the security of the SAML configuration. You just simply need to copy and paste your own Public key and Private key in this section.
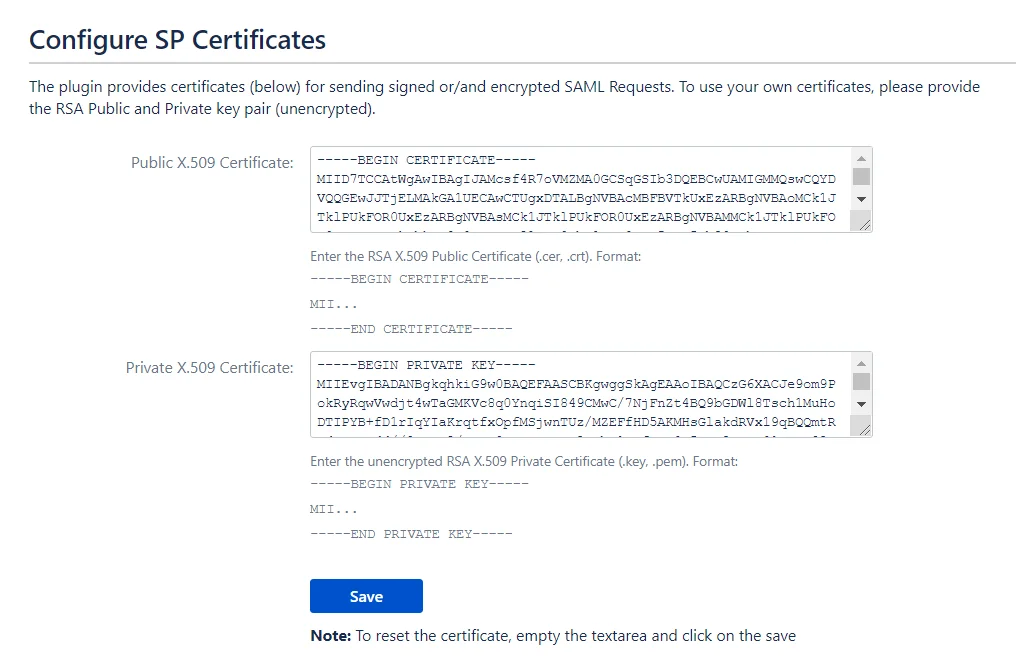
Steps to Configure Custom Public and Private Certificates
- Generate Custom Certificates. Refer to this document to generate your own certificates.
- After generating the certificates, go to your IdP and update the X.509 certificate that you have set up on your IdP with the newly created public certificate, or contact your IdP team to change the certificate.
- Paste the Public and Private Certificates on this page. Make sure that the certificates are entered in the proper format as given below.
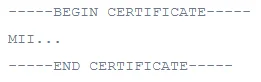
1. Format for Public Certificate :
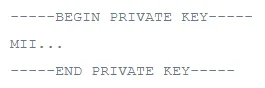
2. Format for Private Key :
Important Note: The certificates must be updated simultaneously in both the IdP and the add-on or it will break the SSO.