Settings
The settings tab provides you additional options for the login flow. It allows you to configure SSO for Anonymous users, administrators and to customize or secure the Backdoor/Emergency URL.
How to Configure Settings
To configure settings,
- Click on the Configure button of the app on the Manage Apps window
- Proceed to SSO & Redirection Rules >> Settings
Anonymous Access and Redirect Delay
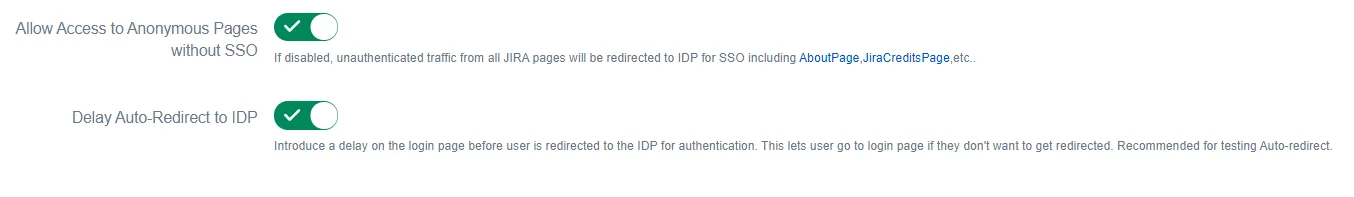
1. Anonymous Access
Some pages in the Atlassian applications can be accessed by unauthenticated traffic like public filters, public spaces, About pages, etc. Also, there are some pages that are not available to unauthenticated users but don’t prompt login and just show an error message.
Disabling Allow Access to Anonymous Pages without SSO switch makes sure that all unauthenticated traffic on your application is prompted for login before being able to view such pages.
2. Delay Auto-Redirect to IDP to IDP
If you have just one IDP set as default IDP in the Redirection Rules, the user is redirected for SSO as soon as he accesses the application. To add a delay here, you can enable this option. In this case, a progress bar will be shown on the login page which will allow users to cancel redirection and use application credentials to log in.
Administrator Login
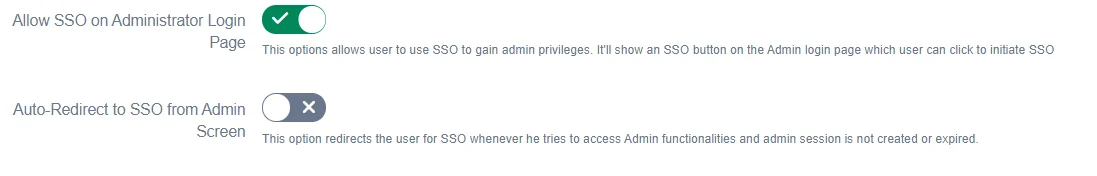
1. Allow SSO on Administrator Login Page
When the administrator logs in and accesses admin functionalities, the admin is prompted for credentials again. Enabling this option makes sure that if the Admin logs in using SSO, he’ll be allowed to use SSO for accessing admin functionalities.
Disable this option, if you want the admin to always use application credentials to access admin functionalities.
2. Auto-Redirect to SSO from Admin Screen
When the admin accesses admin functionality, this option redirects him to the IDP he used to log into the application. This makes sure that all administrators use SSO only to get admin access.
Backdoor/Emergency Login
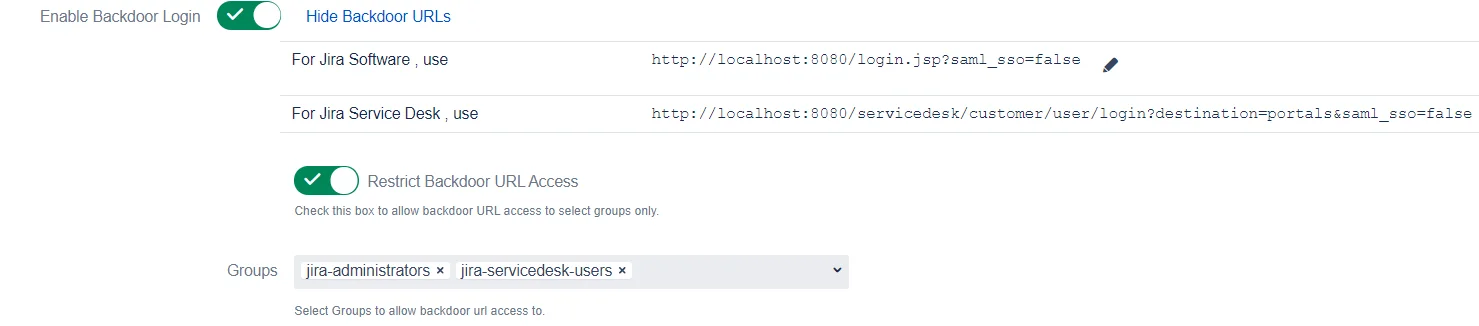
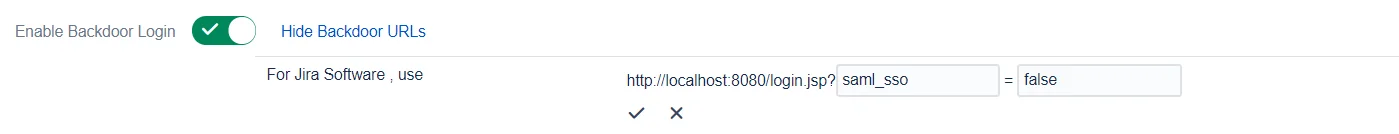
Backdoor/Emergency URL
Backdoor/Emergency URL can be used by local administrators to access the login page when SSO is enabled. This is useful when you’ve Redirection Rules set or when the Default Rule doesn’t have the login page selected.
You can customize the Backdoor URL by clicking on the edit button beside it and entering new parameter values
Restrict Backdoor URL
You can Restrict the Backdoor URL to certain groups in the application. When you enable this option, you’ll be asked to enter the groups to whom backdoor access should be provided. Now, when a user tries to access the backdoor URL, he’ll be asked for his username first and if that username belongs to the configured group, only then will he be able to use the login page.
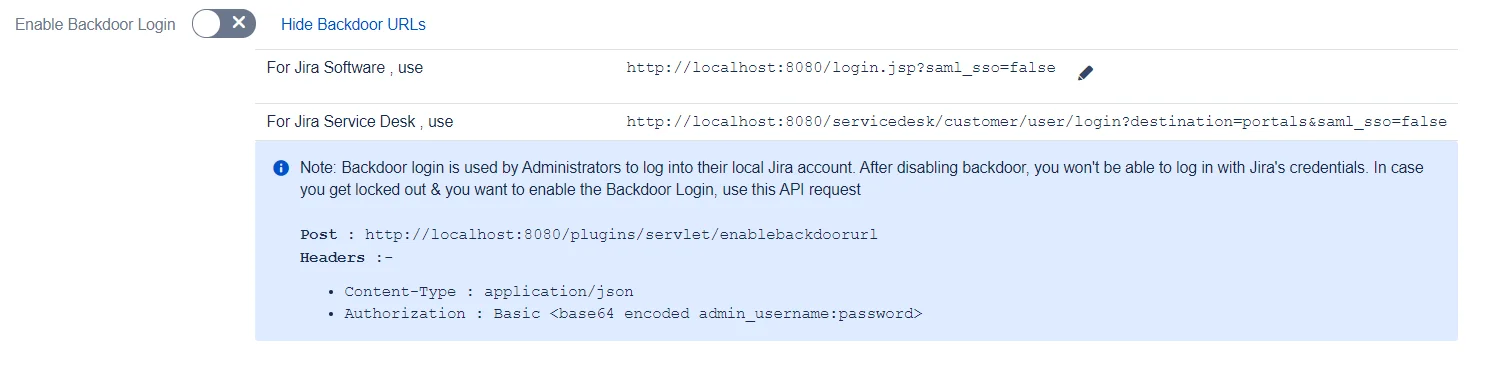
Disable Backdoor Login
The Backdoor Login option is enabled by default. However, you can disable it and enable it only when needed. To do this, you’ll need to call the API /plugins/servlet/enablebackdoorurl with your admin credentials. The details are provided in the app once you disable backdoor login
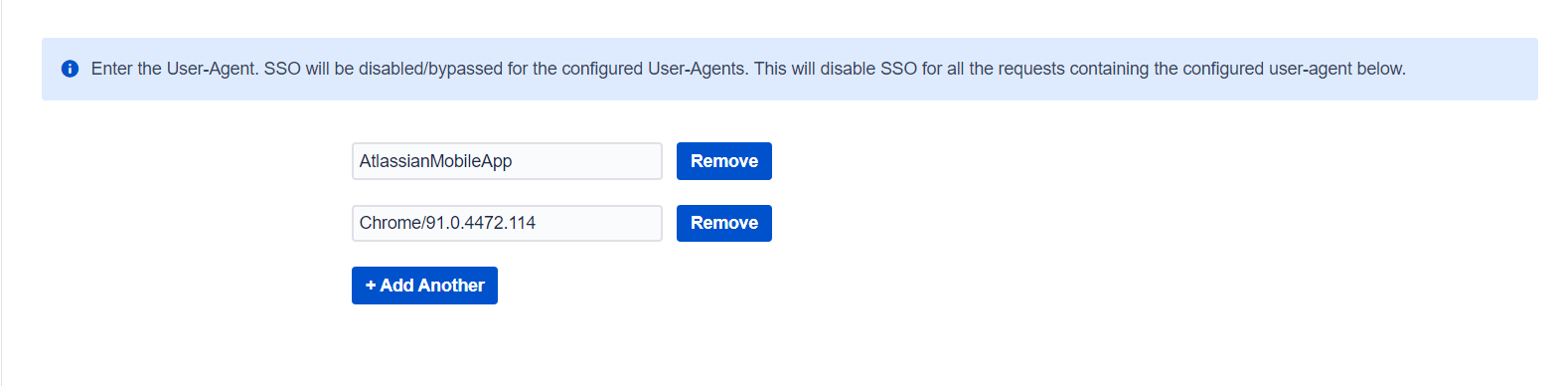
Disable SSO based on user-agent
User-agent based SSO can be used by administrators to skip SSO for a particular user-agent coming in the request. Administrators can configure multiple user-agents for which SSO should not be invoked.
This is useful when you want to disable SSO for specific browsers/devices.
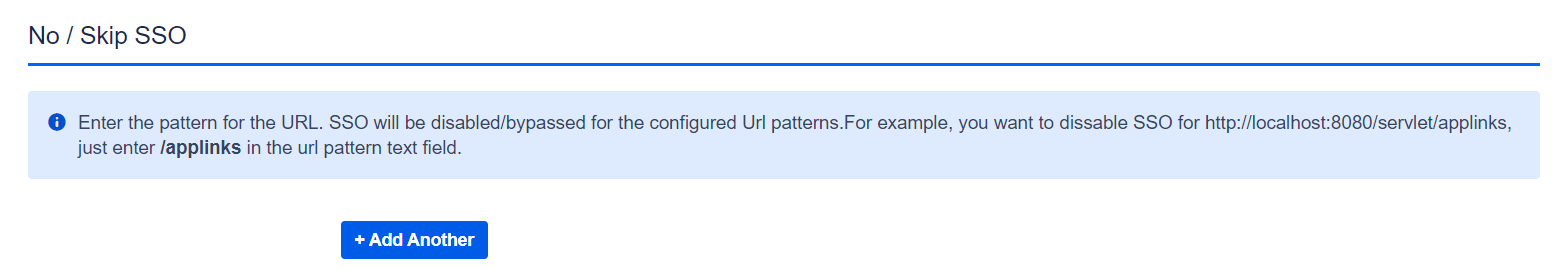
Added option to configure No SSO URL(s)
Sometimes Atlassian applications are integrated with other applications to share some information and generally these integrations work on top of basic authentication and use local user accounts (service accounts). In this case, if we enable force SSO in the miniOrange SSO then all Pages/URLs will be protected with SSO and the app always redirects to IDP for authentication which will break the integration with other applications.
To handle this we have added the No SSO URL(s) option which lets you bypass the SSO for specific URLs that give access to some public resource or redirects to other linked applications, etc.
You need to provide the relative path of the URL like, /resource, /jira etc.