Service Provider Info
To perform the SAML SSO you need to configure both the Identity Provider and the Service Provider. First, you have to create an SSO application on your Identity Provider and provide the details about your Service Provider there. Then you will get the metadata for Identity Provider which will be given to the Service Provider by configuring the IdP on the SSO add-on. Once these 2 steps are over, the connection between your IdP and SP will be complete.
Service Provider Metadata
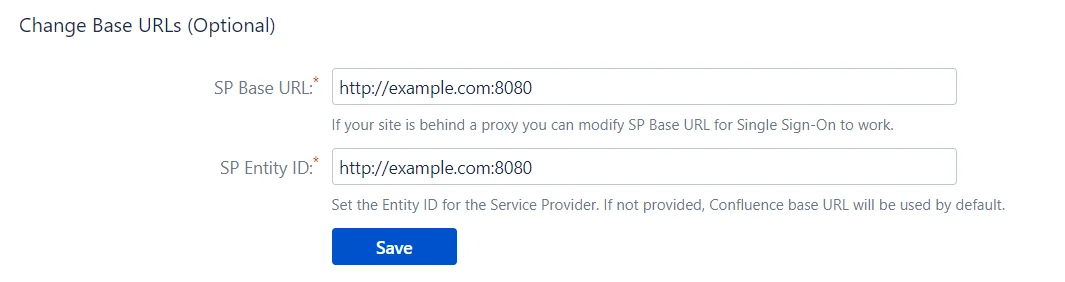
To configure the Service Provider(SP) as an application on the Identity Provider(IdP) some details about the Service Provider are needed. You can find all these details on this Service Provider Info tab of the add-on. You can provide the SP information to your IdP in 3 ways – using Metadata URL, using Metadata XML file or by manually configuring the URLs on IDP.
Metadata URL: The Metadata URL provides the application’s SAML Metadata information that can be used to configure the application in the IdP as a SP in one go. The provided metadata url will be in this format : <Application Base URL>/plugins/servlet/saml/metadata
Metadata XML: This file contains all the information about the SP in an XML format. If the IdP supports importing the metadata from a file, then you can configure the application on your IdP in minutes by just uploading this metadata file.
Configure IDP manually: You have the option of configuring your IdP manually using the SP URLs displayed this Service Provider Info tab. You will need to copy and paste the required URLs from the table into your IDP SAML Configuration to add the application as a SAML SP. Most SAML 2.0 Identity Providers will require the following URLs to configure an application :
- SP Entity ID/Issuer: This URL will be used to uniquely identify your Service Provider. It basically identifies the Service Provider for which the SAML assertions or responses are intended. Some IdPs also refer to this URL as Audience URL.
- ACS URL: This URL is often referred to as the Service Provider (SP) sign-in URL. This is the URL to which the IDP will send the SAML response or SAML assertion after successful authentication. Some IdPs also refer to this URL as Recipient URL or Destination URL.
- Single Logout URL: If your IDP supports it, this URL can be used to configure Single Logout. This feature allows the user to be logged out from both IDP and Service Provider if the user logs out from either the IDP or the Service Provider. When a user initiates a logout, the identity provider logs the user out of all applications in the current identity provider login session.
- Certificate: This certificate is used by the IdPs to validate the requests and to encrypt the responses. Some IdPs mandate the SPs to send signed requests so that they can verify that the requests are coming from the expected SPs. So whenever an IdP receives a SAML request, they use this certificate to validate the sender of that signed request. This certificate is also used by IdPs to send the SAML response in the encrypted format so that only SP can decrypt it using the private key and no one else gets access to the sensitive user information sent in the response/assertion. You can configure and use your own certificates to increase the security from the ‘Certificates Tab’ of the add-on.
Customize the SP Metadata(Optional)
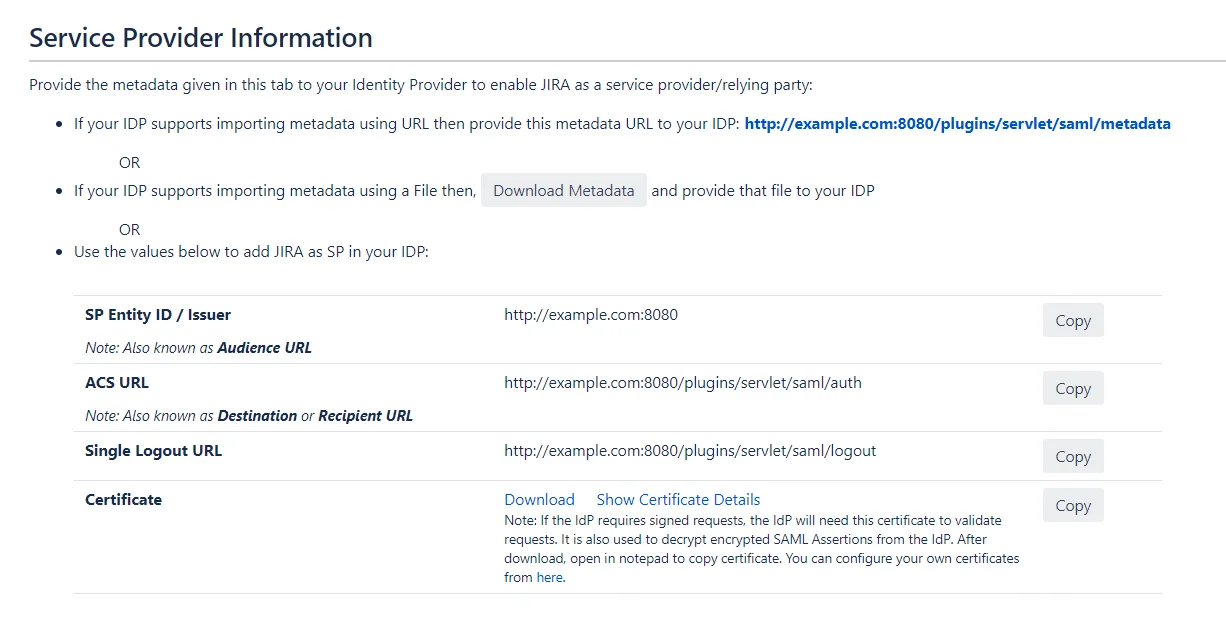
You can customize the SP metadata according to you using the Customize Metadata feature. When you click on this button you will see a popup showing all the fields in the metadata that can be customized. In the pop-up form you will find fields to add your organization details along with technical and support contact details. Along with these fields, there are options to choose which certificates will be sent in the metadata. Depending on the features supported by the IDP, the plugin can sign the request and decrypt authentication responses for better security and stronger validation. The options provided are :
- Include Signing Certificate in Metadata: If enabled, public certificate of the plugin will be added in the Service Provider Metadata and it will be used by the IDP to verify the Signature in the SAML Request from the application.
- Include Encryption Certificate in Metadata: If enabled, public encryption certificate of the plugin will be added in the Service Provider Metadata that will be used by the IDP to encrypt the SAML Response.
Change SP Base URLs (Optional)
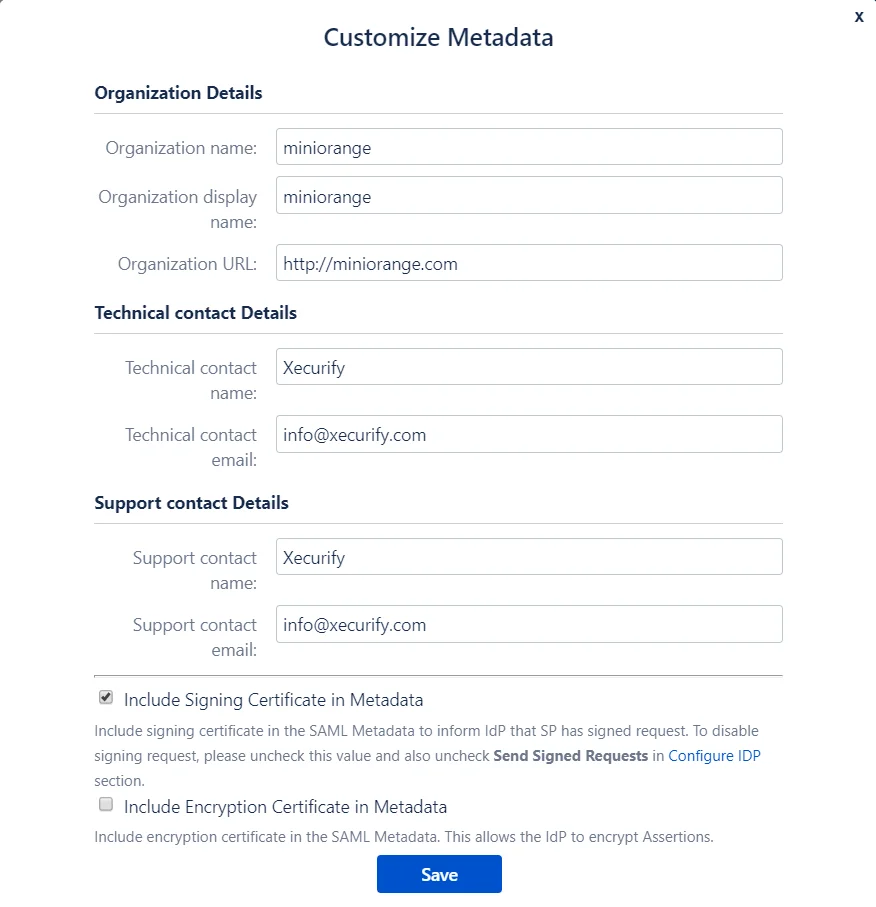
The add-on allows you to change the SP BASE URL and SP ENTITY ID to values other than the set defaults.
- SP Base URL: Typically all the Service Provider SAML endpoints are generated based on the Service Provider’s Base URL. If your Atlassian application is running behind a proxy, then your base URL will be different from the present value. You can update the SP(Service Provider) Base URL according to your proxy using this option. Updating this will also update URLs in the metadata so SP information has to be re-configured in IdP again.
- SP Entity ID: It also referred to as Issuer. It is used by the Identity Provider to uniquely identify your Atlassian application.