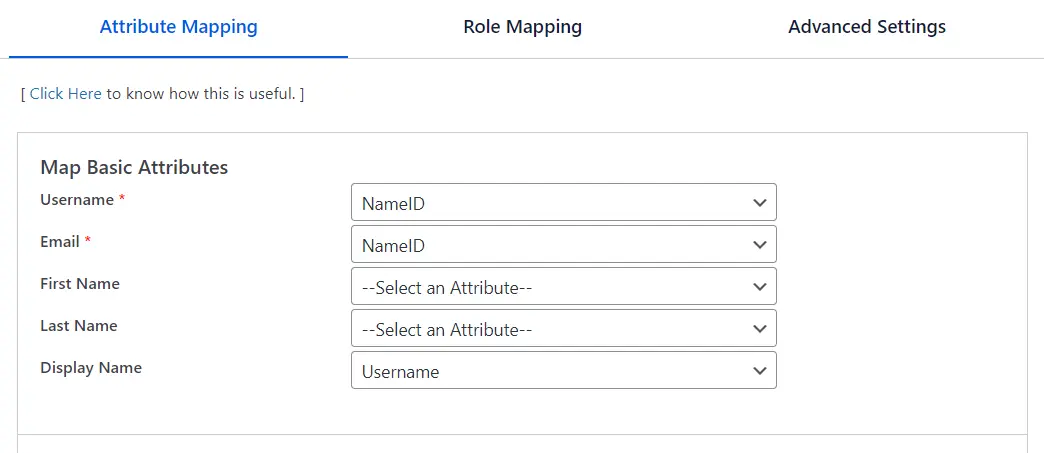
1. Attribute Mapping
Attributes are the user details that are stored in your Identity Provider like Okta, Keycloak, Azure AD, etc . These attributes include Username, Email, First Name, Last Name, Group/Role, Display Name, etc. The Attribute Mapping feature helps you to map these user attributes sent by the IDP to the WordPress user attributes.
- Everytime your users SSO into your WordPress site, these attributes will be automatically mapped to your WordPress user profile.
- If any existing user performs the SSO, then their wordpress account will be fetched and their profile details will be overridden by the attributes received from the IDP.
- By default, the Username and Email are the two basic attributes that are used for attribute mapping. Generally, the NameID value is what’s used for this purpose.
- You can choose and set attributes sent by the IDP to be mapped with WordPress attributes like FirstName, LastName, DisplayName.
- The Group/Role field can be used as a group transformation attribute. You can map the Group/Role field to the attribute name in which IDP is sending the users Security Group or Membership Information.
- Depending on the value of the Group attribute, you can assign single or multiple wordpress roles to the users. The custom roles are also supported for the mapping. Please refer to the role mapping section for more information.
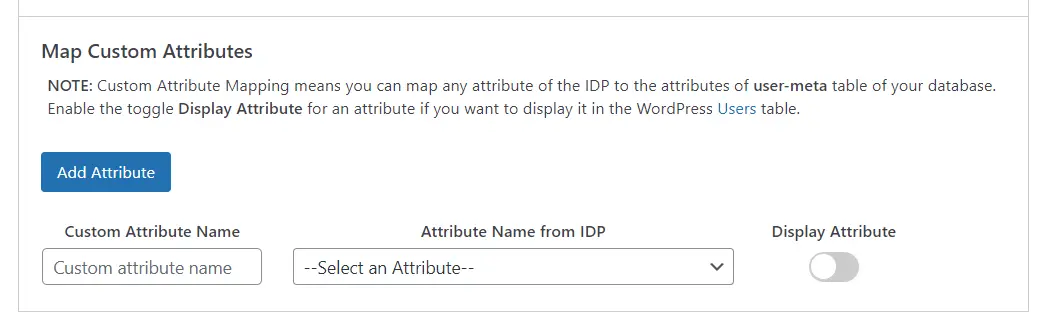
Map Custom Attributes
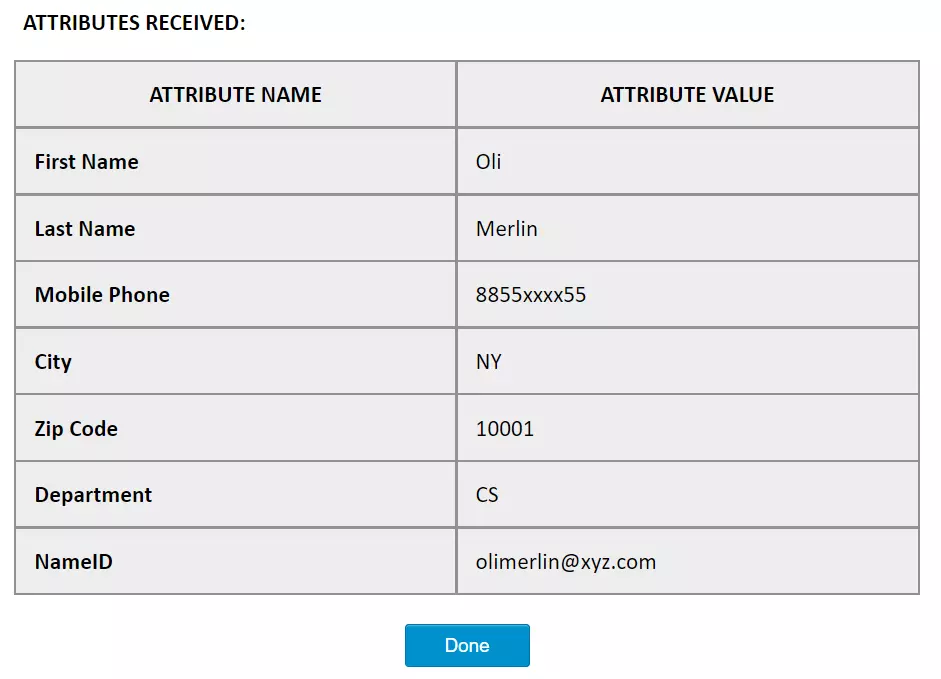
- It provides an additional feature to Map Custom Attributes (ACF - Advanced Custom Fields) to the wordpress users. Using this feature you can map and store additional attributes received from the IDP to the wordpress user_meta table.
For eg.; A user has a custom attribute as Address, then in the database (i.e. user_meta table), it will be stored against the userID of that specific user. - For eg., if you want to map attributes like Phone no., City, State, Department etc., you will simply have to add these attributes in your IDP and set them up into your Custom attribute mapping to map with their equivalent attributes as shown in the image below, the attributes which are sent from the Identity Provider appropriately added and mapped to their equivalent attributes in the wordpress site.
Display Custom Attributes
- You can enable the Display Attribute option for an attribute if you want to display it in the Wordpress Users menu.
2. Domain Restriction
- This functionality, located within the Advanced Settings tab, allows you to restrict/allow user access to the wordpress site based on the domain of their email address.
- For the WordPress Multisite SSO Plugin, you can also restrict which group of users will have access to which subsite based on the domain of the user.
- You can provide multiple domains to restrict by entering a domain value separated by semicolon(;).
It has the following 2 ways to use this feature :
-
Allow users to login with specified domains : If enable this feature then only the users of specified domains will be allowed to login or register.
-
Deny users to login with specified domains : If enable this feature then users of specified domains will be restricted to login. Remaining all the users will be allowed to login.
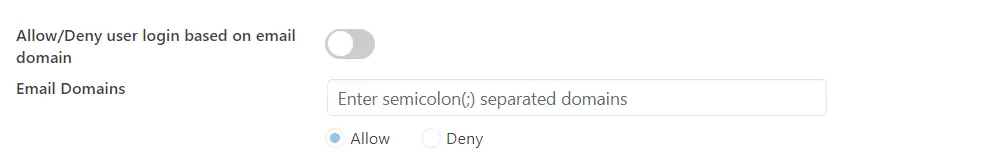
- Now, for eg. If you want users of miniOrange (i.e. miniorange.com) to not log in to your site, then you can simply enter miniorange.com in the input tag and enable the toggle Allow/Deny user login based on email domain and select Deny radio button, if want to Deny the specified email domain.
3. Role Mapping
- This feature can be used to assign different WordPress roles to the users based on their SAML attributes. The particular roles will be applied to users once they meet the specified conditions while logging into WordPress via Single Sign-On.
- This feature allows you to provide user capabilities based on their IdP attribute Group values.
- Before enabling this setting, please make sure you’ve configured the attribute name in the Group/Role field of the Attribute Mapping section.
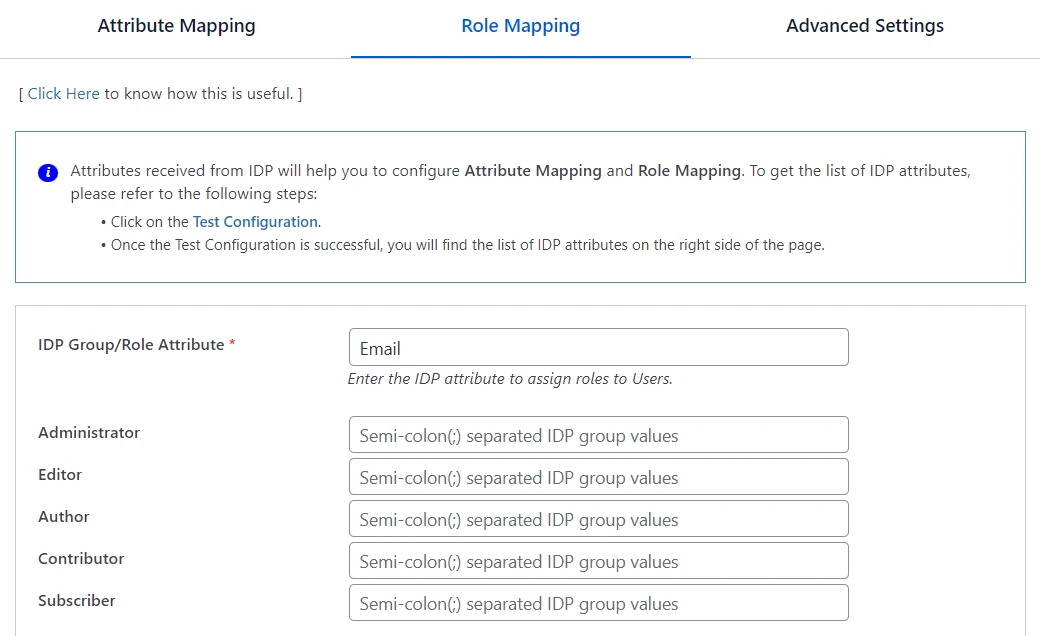
WordPress has 5 pre-defined roles :
- Administrator
- Editor
- Author
- Contributor
- Subscriber
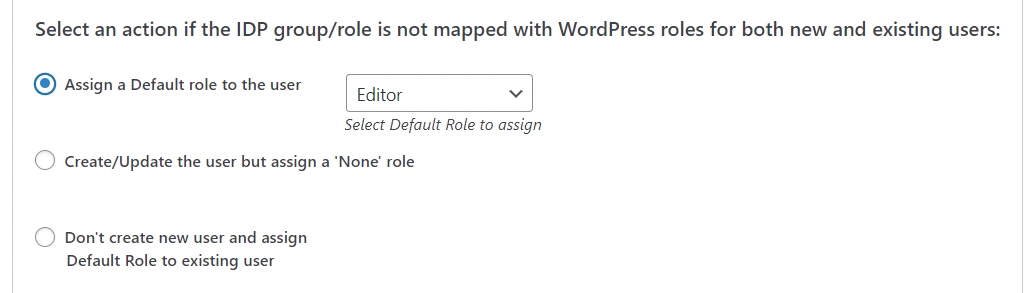
This section allows you to select an action if the IDP group/role is not mapped with WordPress roles for both new and existing user.
Note: This section will be enabled only if you have configured the Role mapping as specified in the above step.
-
Assign a Default role to the user: This feature is used to set a default role to users who are not mapped here. It will automatically set the default role to the new users.You can choose any of the roles listed to be set as default.
-
Create/Update the user but assign a 'None' role: Enabling this toggle will assign the role "None" to both new users and existing users (users already created in WordPress), if no role is assigned to the user in the role mapping.
-
Do not create the user: If the admin wants to create the users on the WordPress site only if their groups are mapped, then this feature can be enabled. This won’t allow unmapped new users to access the site.
-
Apply all role mapping settings to WP admin users: By default role mapping will be applied only to non-admin users (users that do NOT have Administrator roles). You will have to enable this option to apply role mapping to Administrator users.

4. Advanced Settings
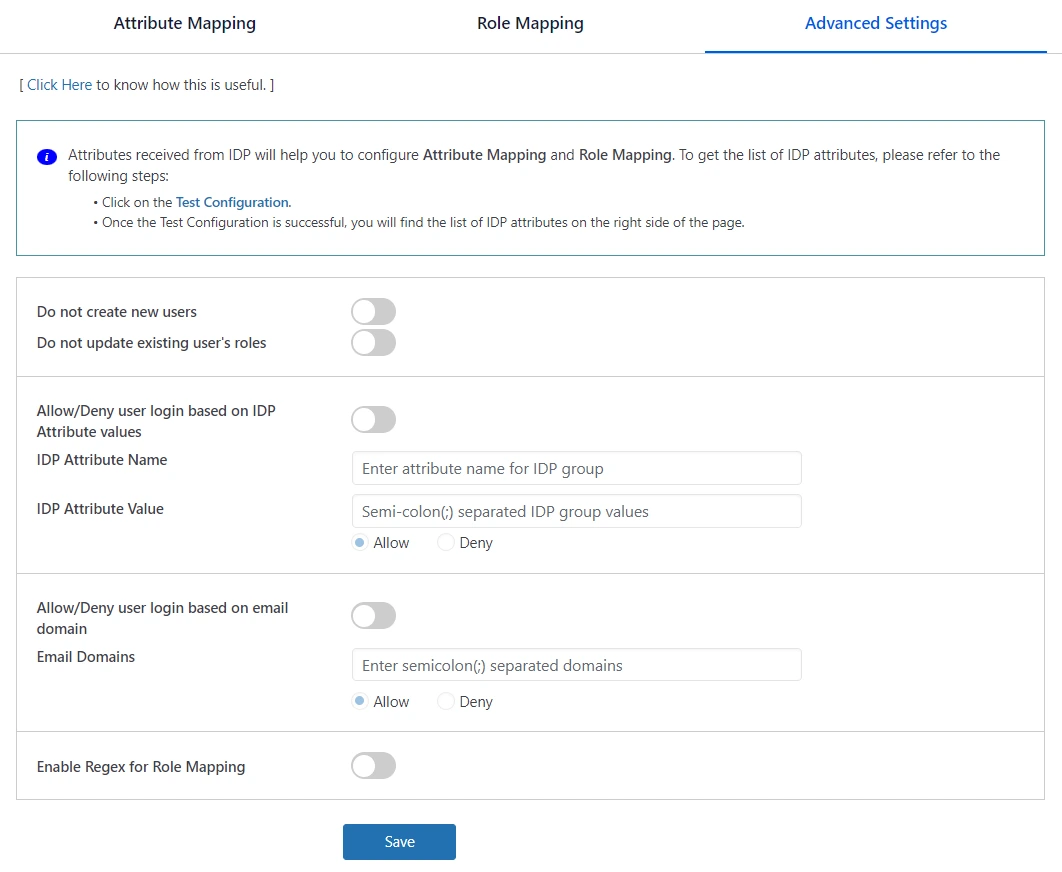
- Do not create new users: Enabling this toggle will prevent new users from logging in and being created in WordPress. However, existing users (users already created in WordPress) will still be able to perform single sign-on (SSO).
- Do not update existing user's roles: By enabling this toggle, the roles of the existing users (users already created in WordPress) will not change.
- Allow/Deny user login based on email domain: If you want the users of a specific domain to be allowed or restricted to login then you can use this feature. Note: The users will be restricted/allowed to login based on their Email Attribute as mapped in the Attribute Mapping section.
- Allow/Deny user login based on IDP Attribute values: Enabling this toggle will determine, whether users will be allowed or denied to login on the basis of the below option selected and mapped IDP group attribute value.
- Enable Regex: Enabling this toggle allows you to set up patterns in the role mapping instead of IDP group values, so users will be assigned roles based on the specified pattern.
For more information visit our WordPress SSO page.